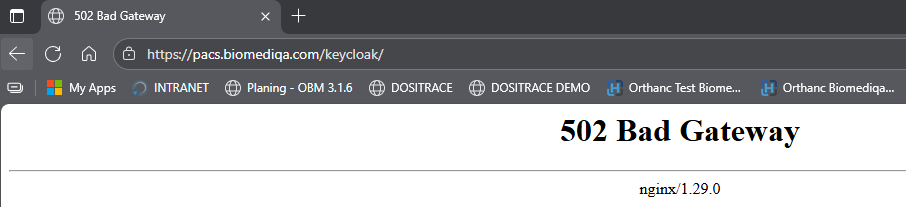
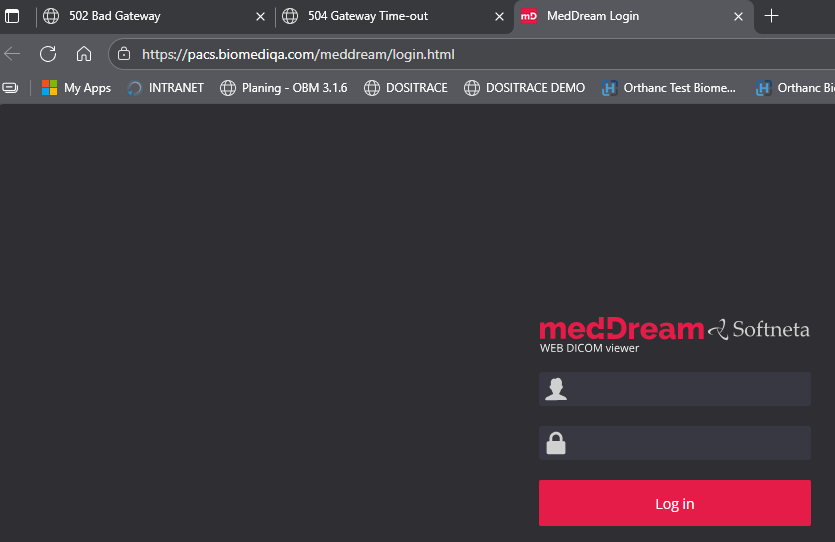
I am trying to set up my Orthanc server, however I cannot even access the keycloak auth page. I am expecting the keycloak auth interface at https://pacs.biomediqa.com
My configurations so far
nginx
server {
server_name biomediqa.com pacs.biomediqa.com;
# Common settings for handling large files, headers, and buffer sizes
# To avoid 504 error when uploading big files
proxy_read_timeout 60s;
# To avoid "too big header... / 502 Bad Gateway" error
proxy_buffer_size 32k;
proxy_buffers 64 8k;
proxy_busy_buffers_size 48k;
# To avoid "414 Request-URI Too Large" when opening multiple studies in OHIF
large_client_header_buffers 8 16k;
# Location for Keycloak Authentication
# Location for Keycloak Authentication
location /keycloak/ {
# Forward requests to the Keycloak authentication server
proxy_pass https://pacs.biomediqa.com/auth/realms/orthanc/account;
# Rewrite the URL to match expected Keycloak path
rewrite ^/keycloak/(.*) /$1 break;
# Set necessary headers for Keycloak
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
# Disable proxy request buffering
proxy_request_buffering off;
proxy_max_temp_file_size 0;
# Set client size limits for large requests
client_max_body_size 0;
}
# Default redirect for the root location
location / {
return 301 /orthanc/ui/app/;
}
# Location for Orthanc
location /orthanc/ {
proxy_pass http://orthanc:8042;
rewrite /orthanc(.*) $1 break;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
# Location for OHIF viewer
location /ohif/ {
proxy_pass http://ohif:80;
rewrite /ohif(.*) $1 break;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/pacs.biomediqa.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/pacs.biomediqa.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
add_header Strict-Transport-Security "max-age=31536000" always; # managed by Certbot
ssl_trusted_certificate /etc/letsencrypt/live/pacs.biomediqa.com/chain.pem; # managed by Certbot
ssl_stapling on; # managed by Certbot
ssl_stapling_verify on; # managed by Certbot
}
server {
if ($host = pacs.biomediqa.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
listen [::]:80;
index index.html index.htm index.nginx-debian.html;
server_name biomediqa.com pacs.biomediqa.com;
location / {
try_files $uri $uri/ =404;
proxy_buffer_size 128k;
proxy_buffers 4 256k;
proxy_busy_buffers_size 256k;
}
}
Orthanc
services:
nginx:
image: orthancteam/orthanc-nginx-certbot:main
depends_on: [orthanc, orthanc-auth-service, keycloak]
restart: unless-stopped
#ports: ["80:80"]
ports: ["443:443"]
volumes:
- /etc/letsencrypt/live/pacs.biomediqa.com/fullchain.pem:/etc/letsencrypt/live/pacs.biomediqa.com/fullchain.pem
- /etc/letsencrypt/live/pacs.biomediqa.com/privkey.pem:/etc/letsencrypt/live/pacs.biomediqa.com/privkey.pem
- /etc/letsencrypt/live/pacs.biomediqa.com/chain.pem:/etc/letsencrypt/live/pacs.biomediqa.com/chain.pem
- /etc/nginx/sites-enabled/pacs.biomediqa.com.conf:/etc/nginx/sites-enabled/pacs.biomediqa.com.conf
- /etc/nginx/sites-available/pacs.biomediqa.com.conf:/etc/nginx/sites-available/pacs.biomediqa.com.conf
environment:
ENABLE_ORTHANC: "true"
ENABLE_KEYCLOAK: "true"
ENABLE_ORTHANC_TOKEN_SERVICE: "false"
ENABLE_HTTPS: "true"
ENABLE_MEDDREAM: "true"
ENABLE_ORTHANC_FOR_API: "true"
ENABLE_OHIF: "true"
DOMAIN_NAME: "pacs.biomediqa.com"
CERTBOT_EMAIL: "hidden"
CERTBOT_AUTHENTICATOR: "nginx"
orthanc:
image: orthancteam/orthanc
depends_on: [postgres]
volumes:
- orthanc-storage:/var/lib/orthanc/db:Z
restart: unless-stopped
environment:
ORTHANC__NAME: "Orthanc"
VERBOSE_ENABLED: "true"
VERBOSE_STARTUP: "true"
VOLVIEW_PLUGIN_ENABLED: "true"
ORTHANC_JSON: |
{
"OrthancExplorer2": {
"UiOptions": {
"StudyListSearchMode": "search-button",
"StudyListContentIfNoSearch": "empty",
"ShowSamePatientStudiesFilter": ["PatientBirthDate", "PatientID"],
"MedDreamViewerPublicRoot": "https://pacs.biomediqa.com/meddream/",
"EnableApiViewMenu": true,
"EnableShares": true,
"DefaultShareDuration": 90,
"ShareDurations": [0, 7, 15, 30, 90, 365],
"EnableOpenInOhifViewer3": true,
"EnableOpenInMedDreamViewer": true,
"OhifViewer3PublicRoot": "https://pacs.biomediqa.com/ohif/"
},
"Tokens" : {
"InstantLinksValidity": 3600,
"ShareType": "meddream-viewer-publication"
},
"Keycloak" : {
"Enable": true,
"Url": "https://pacs.biomediqa.com/keycloak/",
"Realm": "orthanc",
"ClientId": "orthanc"
}
},
"DicomWeb": {
"PublicRoot": "/orthanc/dicom-web/"
},
"StoneWebViewer": {
"ShowInfoPanelAtStartup": "Never"
},
"PostgreSQL": {
"Host": "postgres"
},
"AuthenticationEnabled": false, // because it is handled by the authorization plugin
"Authorization": {
"WebServiceRootUrl": "http://orthanc-auth-service:8000/",
"WebServiceUsername": "biomediqa",
"StandardConfigurations" : [
"stone-webviewer",
"orthanc-explorer-2",
"ohif",
"volview"
],
"CheckedLevel": "studies",
"TokenHttpHeaders" : [ "api-key" ],
"UncheckedResources" : [
"/app/images/unsupported.png"]
}
}
secrets:
- ORTHANC__AUTHORIZATION__WEB_SERVICE_PASSWORD
postgres:
image: postgres:16
restart: unless-stopped
volumes:
- orthanc-db:/var/lib/postgresql/data:Z
environment:
POSTGRES_HOST_AUTH_METHOD: "trust"
orthanc-auth-service:
image: orthancteam/orthanc-auth-service:main
depends_on: [keycloak]
restart: unless-stopped
environment:
ENABLE_KEYCLOAK: "true"
PUBLIC_ORTHANC_ROOT: "https://pacs.biomediqa.com/orthanc/"
PUBLIC_LANDING_ROOT: "https://pacs.biomediqa.com/orthanc/ui/app/token-landing.html"
PERMISSIONS_FILE_PATH: "/orthanc_auth_service/permissions.json"
ENABLE_KEYCLOAK_API_KEYS: "true"
PUBLIC_OHIF_ROOT: "https://pacs.biomediqa.com/ohif/"
MEDDREAM_TOKEN_SERVICE_URL: "http://meddream-token-service:8088/v3/generate"
PUBLIC_MEDDREAM_ROOT: "https://pacs.biomediqa.com/meddream/"
env_file:
- ./secrets/orthanc-token.secret.env
secrets:
- SECRET_KEY
- KEYCLOAK_CLIENT_SECRET
volumes:
- ./permissions.json:/orthanc_auth_service/permissions.json
ohif:
image: orthancteam/ohif-v3:main
volumes:
- ./ohif-app-config.js:/usr/share/nginx/html/app-config.js
restart: unless-stopped
meddream-token-service:
image: orthancteam/meddream-token-service:main
restart: unless-stopped
meddream-viewer:
image: orthancteam/meddream-viewer:main
restart: unless-stopped
depends_on:
- orthanc-for-api
environment:
integration: "study"
TOKEN_SERVICE_ADDRESS: "http://meddream-token-service:8088/v3/validate"
ORTHANC_BASE_URL: "http://orthanc-for-api:8042"
ORTHANC_USER: "orthanc"
MEDDREAM_PACS_CONFIG_TYPE: "Dicomweb"
env_file:
- ./secrets/meddream.secret.env
volumes:
- meddream-license:/opt/meddream/license
# An orthanc dedicated for API accesses and also used by MedDream
orthanc-for-api:
image: orthancteam/orthanc
volumes:
- orthanc-storage:/var/lib/orthanc/db:Z
- ./meddream-plugin.py:/scripts/meddream-plugin.py
depends_on: [postgres]
restart: unless-stopped
environment:
ORTHANC__NAME: "Orthanc for API"
ORTHANC__DATABASE_SERVER_IDENTIFIER: "orthanc2"
VERBOSE_ENABLED: "true"
VERBOSE_STARTUP: "true"
ORTHANC__AUTHENTICATION_ENABLED: "true"
DICOM_WEB_PLUGIN_ENABLED: "true"
ORTHANC__DICOM_WEB__PUBLIC_ROOT: "/orthanc-api/dicom-web/"
ORTHANC__POSTGRESQL__HOST: "postgres"
ORTHANC__POSTGRESQL__INDEX_CONNECTIONS_COUNT: 40
ORTHANC__ORTHANC_EXPLORER_2__UI_OPTIONS__MED_DREAM_VIEWER_PUBLIC_ROOT: "https://pacs.biomediqa.com/meddream/"
secrets:
- orthanc-api.secret.json
keycloak:
image: orthancteam/orthanc-keycloak:main
depends_on: [keycloak-db]
restart: unless-stopped
environment:
KC_BOOTSTRAP_ADMIN_USERNAME: "admin"
KC_DB: "postgres"
KC_DB_URL: "jdbc:postgresql://keycloak-db:5432/keycloak"
KC_DB_USERNAME: "keycloak"
KC_DB_PASSWORD: "keycloak"
KC_HOSTNAME: "https://pacs.biomediqa.com/keycloak"
secrets:
- KC_BOOTSTRAP_ADMIN_PASSWORD
keycloak-db:
image: postgres:16
restart: unless-stopped
volumes:
- keycloak-db:/var/lib/postgresql/data
environment:
POSTGRES_PASSWORD: "keycloak"
POSTGRES_USER: "keycloak"
POSTGRES_DB: "keycloak"
volumes:
keycloak-db:
orthanc-storage:
orthanc-db:
meddream-license:
secrets:
ORTHANC__AUTHORIZATION__WEB_SERVICE_PASSWORD:
file: ./secrets/ORTHANC__AUTHORIZATION__WEB_SERVICE_PASSWORD
SECRET_KEY:
file: ./secrets/SECRET_KEY
KEYCLOAK_CLIENT_SECRET:
file: ./secrets/KEYCLOAK_CLIENT_SECRET
KC_BOOTSTRAP_ADMIN_PASSWORD:
file: ./secrets/KC_BOOTSTRAP_ADMIN_PASSWORD
orthanc-api.secret.json:
file: ./secrets/orthanc-api.secret.json