Hi everyone,
after testing the docker compose via orthanc-team / orthanc-auth-service, I decided to test with my external keycloak server instead using the local one. However, I got some issue on the set up.
- I use the nginx image and update my defaults.conf
# SPDX-FileCopyrightText: 2022 - 2024 Orthanc Team SRL <info@orthanc.team>
#
# SPDX-License-Identifier: CC0-1.0
server {
listen 80;
# Common settings for handling large files, headers, and buffer sizes
# To avoid 504 error when uploading big files
proxy_read_timeout 60s;
# To avoid "too big header... / 502 Bad Gateway" error
proxy_buffer_size 32k;
proxy_buffers 64 8k;
proxy_busy_buffers_size 48k;
# To avoid "414 Request-URI Too Large" when opening multiple studies in OHIF
large_client_header_buffers 8 16k;
# Location for Keycloak Authentication
# Location for Keycloak Authentication
location /keycloak/ {
# Forward requests to the Keycloak authentication server
proxy_pass https:/my_keycloak_server/auth;
# Rewrite the URL to match expected Keycloak path
rewrite ^/keycloak/(.*) /$1 break;
# Set necessary headers for Keycloak
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
# Disable proxy request buffering
proxy_request_buffering off;
proxy_max_temp_file_size 0;
# Set client size limits for large requests
client_max_body_size 0;
}
# Default redirect for the root location
location / {
return 301 /orthanc/ui/app/;
}
# Location for Orthanc
location /orthanc/ {
proxy_pass http://orthanc:8042;
rewrite /orthanc(.*) $1 break;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
# Location for OHIF viewer
location /ohif/ {
proxy_pass http://ohif:80;
rewrite /ohif(.*) $1 break;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
}
Then, I update my keycloak config under ORTHANC_JSON
"Keycloak": {
"Enable": true,
"Url": "https://my_keycloak_server/auth",
"Realm": "myrealm",
"ClientId": "orthanc-dev"
}
for the orthanc-auth-service setup, I noticed that there is default values assigned to the KEYCLOAK_ADMIN_URI, so I empty it out
SECRET_KEY: "password"
ENABLE_KEYCLOAK: "true"
KEYCLOAK_URI: "https://my_keycloak_server/auth/realms/myrealms/"
# ENABLE_KEYCLOAK_API_KEYS: "true"
# # to enable the permissions edition UI in OE2, you need to provide a KEYCLOAK_CLIENT_SECRET
# KEYCLOAK_CLIENT_SECRET: "change-me-I-am-a-secret-you-get-in-keycloak-logs"
KEYCLOAK_CLIENT_SECRET: "xyxyxyyxyxyxyxyyxyxyxyyxyxyyxyyxyxx"
KEYCLOAK_ADMIN_URI: ""
When I visit my server ip on browser, it try to redirect me to my keycloak but it keep saying Invalid parameter: redirect_uri. When I visit ip/keycloak, it is not redirecting me to the keycloak login page.
I am little confused with how I can integrate with the external keycloak server. Could you give me some suggestion how to do it?
Thank you!
Hello,
There is a discrepancy between the 2 parts of the config you quoted:
myrealm
"Keycloak": {
"Enable": true,
"Url": "https://my_keycloak_server/auth",
"Realm": "myrealm",
myrealmS
SECRET_KEY: "password"
ENABLE_KEYCLOAK: "true"
KEYCLOAK_URI: "https://my_keycloak_server/auth/realms/myrealms/"
That being said, if ip/keycloak doesn’t show your keycloak instance, the problem is on the Nginx or the Keycloak side.
I would:
- check the nginx logs to see if the query goes to the right place
- compare your keycloak configuration with the configuration of the keycloak we provide
I hope this helps,
Cheers,
Hello,
Currently when I access my server IP, it will redirect me to the SSO page. However, once I login, it redirects me to IP/orthanc/ui/app/#/ but it is a blank page.
Do you know if there is a config issue with my nginx or on the keycloak?
Here is my updated nginx.conf
# SPDX-FileCopyrightText: 2022 - 2024 Orthanc Team SRL <info@orthanc.team>
#
# SPDX-License-Identifier: CC0-1.0
server {
listen 80;
# Common settings for handling large files, headers, and buffer sizes
# To avoid 504 error when uploading big files
proxy_read_timeout 60s;
# To avoid "too big header... / 502 Bad Gateway" error
proxy_buffer_size 32k;
proxy_buffers 64 8k;
proxy_busy_buffers_size 48k;
# To avoid "414 Request-URI Too Large" when opening multiple studies in OHIF
large_client_header_buffers 8 16k;
# Location for Keycloak Authentication
# Location for Keycloak Authentication
location /auth/ {
# Forward requests to the Keycloak authentication server
proxy_pass https://broker.id.keycloak.server/auth/realms/myrealm/account;
# Rewrite the URL to match expected Keycloak path
rewrite ^/auth/(.*) /$1 break;
# Set necessary headers for Keycloak
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
# Disable proxy request buffering
proxy_request_buffering off;
proxy_max_temp_file_size 0;
# Set client size limits for large requests
client_max_body_size 0;
}
# Default redirect for the root location
location / {
return 301 /orthanc/ui/app/;
}
# Location for Orthanc
location /orthanc/ {
proxy_pass http://orthanc:8042;
rewrite /orthanc(.*) $1 break;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
# Location for OHIF viewer
location /ohif/ {
proxy_pass http://ohif:80;
rewrite /ohif(.*) $1 break;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Forwarded "for=$proxy_add_x_forwarded_for;proto=$scheme";
proxy_request_buffering off;
proxy_max_temp_file_size 0;
client_max_body_size 0;
}
}
On the keycloak client page, I followed the same setup as the github with
Valid redirect URIs : *
Valid post logout redirect URIs: +
Web origins: *
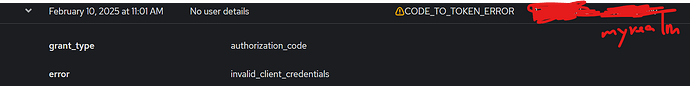
When I checked the events in keycloak, I could see login successful but the next error will be
I have a question regarding default docker compose config
orthanc-auth-service:
image: orthancteam/orthanc-auth-service:25.1.0
# always disable port mapping in production !!!
ports: ["8000:8000"]
# permissions can be customized in the permissions.json file
volumes:
- ./permissions.jsonc:/orthanc_auth_service/permissions.json
depends_on: [keycloak]
restart: unless-stopped
environment:
SECRET_KEY: "change-me-I-am-a-secret-key"
ENABLE_KEYCLOAK: "true"
# ENABLE_KEYCLOAK_API_KEYS: "true"
# # to enable the permissions edition UI in OE2, you need to provide a KEYCLOAK_CLIENT_SECRET
# KEYCLOAK_CLIENT_SECRET: "change-me-I-am-a-secret-you-get-in-keycloak-logs"
KEYCLOAK_CLIENT_SECRET: "qU5qhuToGyKHY4xKcUob5BUePwNBfSoH"
PUBLIC_ORTHANC_ROOT: "http://localhost/orthanc/"
PUBLIC_LANDING_ROOT: "http://localhost/orthanc/ui/app/token-landing.html"
# to use OHIF-plugin: make sure to use http://localhost/orthanc/ohif/
PUBLIC_OHIF_ROOT: "http://localhost/ohif/"
# PUBLIC_OHIF_ROOT: "http://localhost/orthanc/ohif/"
USERS: |
{
"share-user": "change-me"
}
When I login to the keycloak admin page and under the client “Orthanc”, I did not see any setup on the Credential but may I know how could you get the
KEYCLOAK_CLIENT_SECRET: “qU5qhuToGyKHY4xKcUob5BUePwNBfSoH”?
Could you clarify how it is got for the client? I am a bit confused with this part.
Thank you,
Orwanman
Hello,
Here is the part of the documentation you probably are looking for:
Regards,
since I am still using the old method and generate the client secret under the clients, is it still do-able in this way or is it mandatory to use the admin secret for KEYCLOAK_CLIENT_SECRET?